LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
With contributions from Shingo Matsugaya
We delve into three of the most active ransomware families that dominated the first half of 2023: LockBit, Clop, and BlackCat.
Since 2022, our telemetry has consistently pointed to LockBit and BlackCat as two of the most detected RaaS providers.
LockBit’s level of pervasiveness is reflected in a joint cybersecurity advisory from The Cybersecurity and Infrastructure Security Agency (CISA), Federal Bureau of Investigation (FBI), the Multi-State Information Sharing and Analysis Center (MS-ISAC), and other international security bureaus. According to the June 2023 report, one in every six ransomware attacks that targeted US government offices in 2022 was traced back to LockBit actors.
BlackCat also made waves in 2022 as it targeted several high-profile victims that include German oil companies and a European government. Today, all three ransomware families, including Clop, continue to be among the most prolific and evolutionary ransomware families in existence.
This report features data from ransomware-as-a-service (RaaS) and extortion groups’ leak sites, Trend Micro’s open-source intelligence (OSINT) research, and the Trend Micro™ Smart Protection Network™, collected from Jan. 1 to June 30, 2023. It should be noted that we did not include legacy ransomware families, or those that are not visibly active in the current threat landscape, in this report. Legacy ransomware family detections are also excluded from detection counts featured in this report.
Active RaaS, RaaS-related groups, and ransomware victims grew in the first half of 2023
We detected and blocked a total of 6,697,853 ransomware threats across email, URL, and file layers, based on data from our telemetry in the first six months of 2023. This number represents a slight decline of 3.64% compared to the last half of 2022, which had a total detection of 6,950,935.
After analyzing data from ransomware groups’ leak sites, or sites that published attacks on successfully compromised organizations but refused to pay ransom, we observed that the number of RaaS and RaaS-related groups grew by 11.3%.
We also noted that the number of victim organizations surged in the first half of 2023 at 2,001, a 45.27% increase compared to the last half of 2022.
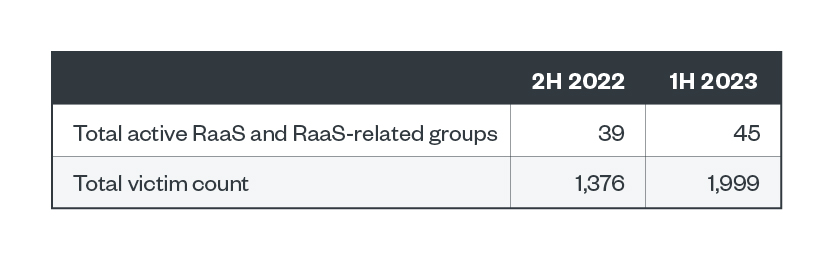
Table 1. The numbers of active RaaS and extortion groups and victim organizations of successful ransomware attacks in the second half of 2022 and the first half of 2023
Sources: RaaS and extortion groups’ leak sites
In the first half of the year, prolific ransomware families topped the list of most active ransomware families
LockBit, Clop, and BlackCat are the three prominent ransomware groups with the greatest number of successful attacks in the first six months of 2023. LockBit, which has managed to remain as the top ransomware family since 2022, accounted for 26.09% of the total number of victim organizations. Meanwhile, 10.59% and 10.09% of attacks belonged to BlackCat and Clop, respectively.
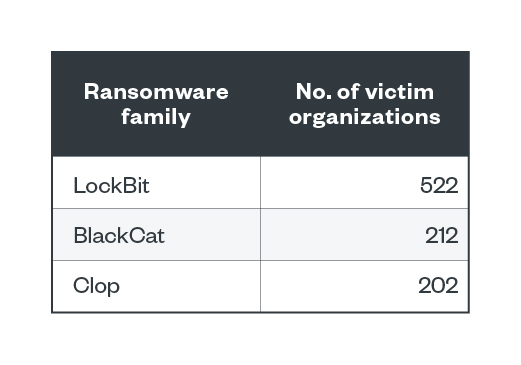
Table 2. The most active ransomware families used in successful RaaS and extortion attacks in terms of victim organizations from Jan. 1 to June 30, 2023
Sources: RaaS and extortion groups’ leak sites
After monitoring attempted ransomware attacks on Trend customers in the first four months of 2023, we saw a continuation of our fourth-quarter observation of LockBit’s activity levels: It appears that LockBit actors’ activity level was typically in the 200-mark per month. However, LockBit attacks ramped up in May and June 2023. Meanwhile, BlackCat attacks started strong in January and February and drastically decreased from March to June this year. We did not detect Clop ransomware attempts on our customers for the first half of 2023.
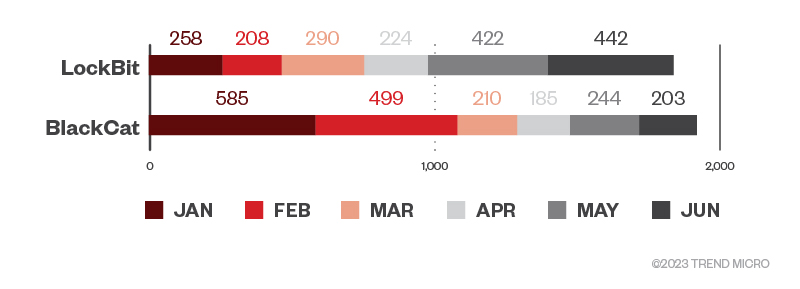
Figure 1. The numbers of ransomware file detections of LockBit, BlackCat, and Clop ransomware in machines per month in the first half of 2023
Source: Trend Micro™ Smart Protection Network™
LockBit’s strong-and-steady lead in the first half of the year was bolstered by high-profile attacks
LockBit’s 18-month lead as the most detected ransomware family is reflected in many noteworthy attacks that made headlines in the first half of the year. In January, Royal Mail, the UK’s largest mail delivery service, suffered from a LockBit attack that effectively halted its international export services.
In February, LockBit actors set their sights on a Dublin-based software company, Ion Group. The LockBit attack rendered “several European and US banks to revert to manual processes.” In April, we discovered how malicious actors deployed LockBit as the malicious payload in the exploitation of two vulnerabilities in the PaperCut software, a widely used print management solution.
Finally, in June 2023, the LockBit gang targeted one of the IT hardware suppliers of the largest contract chipmaker in the world, Taiwan Semiconductor Manufacturing Company (TSMC), and accessed the company’s information. LockBit actors demanded a US$70 million ransom from TSMC; otherwise, they threatened to publish stolen data.
BlackCat claimed prolific attacks, dropped new variant
BlackCat actors, known for their triple-extortion techniques, targeted health IT solutions provider NextGen Healthcare in January 2023. It should be noted that though BlackCat operators put an alleged sample of NextGen information on their extortion site, the Washington Post reported that the operators removed the NextGen listing on their site, and that the alleged BlackCat spokesperson they were in contact with refused to provide proof of the breach.
The BlackCat gang also declared that it was behind the Reddit attack that happened in February this year. The ransomware actors claimed that they’ve stolen 80GB of data, including internal documents, source code, and employee information from the widely popular discussion site. According to reports, BlackCat actors demanded US$4.5 million from Reddit; otherwise, they threatened to leak stolen data.
In the same month, BlackCat operators announced and launched Sphynx, a new BlackCat variant with evolved detection evasion and speed capabilities. In May, we published a report on BlackCat using a new signed kernel driver for evasion based on a BlackCat ransomware infection that also occurred in February.
Clop exploited major vulnerabilities, claimed hundreds of victims
On Jan. 31, 2023, deployed a mass ransomware attack on different organizations that used Fortra’s GoAnywhere file transfer software by exploiting a vulnerability. Clop actors claimed to have compromised 130 organizations in this particular attack, including the City of Toronto and the Community Health Systems (CHS), which is comprised of 80 hospitals, and siphoned off “personal and protected health information of up to 1 million patients.”
Meanwhile, Microsoft’s Threat Intelligence researchers linked the Clop and LockBit gangs to the exploitation of the PaperCut vulnerability to steal corporate data in April 2023. PaperCut is a popular print management software solution that has over 100 million global users.
Back in May 2023, it was reported that FIN7 (aka Sangria Tempest) used the Lizar backdoor to distribute Clop on victims’ machines. Microsoft Research also reported that Clop ransomware actors exploited MOVEit Transfer and MOVEit Cloud vulnerabilities (CVE-2023-34362 and CVE-2023-35036) to compromise big organizations, including Shell and the US Department of Energy.
Small and large enterprises were most targeted in the first half of 2023
Based on our analysis of LockBit’s leak site, more than half of LockBit’s total victims were small businesses (with 200 employees at most), at 57.3%, which was close to the numbers in the fourth quarter of 2022. Midsize businesses (with 201 to 1,000 employees) and large enterprises (with more than 1,000 employees) accounted for 19.7% and 17.4%, respectively.
Meanwhile, almost half — specifically 44.8% — of BlackCat’s victims were small businesses in the first half of 2023. This is followed by midsize businesses at 29.2% and 23.6% of the total victims.
The majority of Clop’s successful attacks targeted large enterprises, accounting for exactly 50% of the total attacks for the first half of 2023. Additionally, small and midsize enterprises made up 27.2% and 21.3% of attacks.
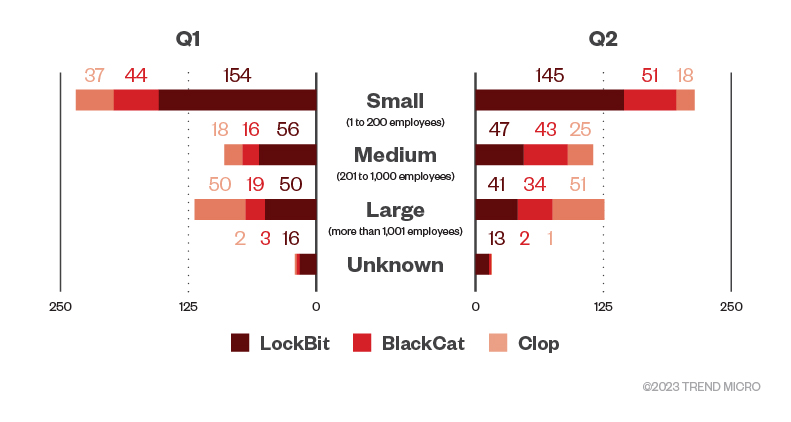
Figure 2. The distribution by organization size of LockBit, BlackCat, and Clop ransomware’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: LockBit, BlackCat, and Clop’s leak sites and Trend's OSINT research
Banking, retail, and transportation industries were in ransomware operators’ crosshairs in the first half of 2023
From January to June 2023, banking, retail, and transportation topped the list of the most targeted industries based on the number of ransomware file detections. From February to June, the banking industry registered the greatest number of ransomware attacks, replacing fast-moving consumer goods (FMCG) as the top targeted industry in the fourth quarter of 2022. Except for March 2023, retail consistently ranked second in terms of detections. Meanwhile, transportation, which had substantial detections from March to May 2023, ranked third.
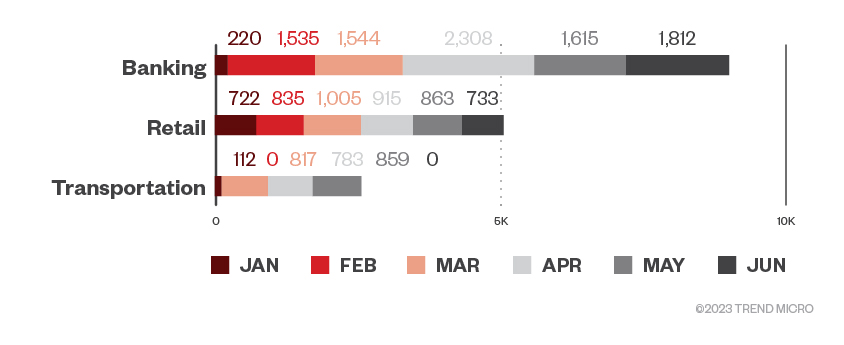
Figure 3. The top three industries in terms of ransomware file detections in machines per month in the first half of 2023
Source: Trend Micro Smart Protection Network
In the first half of 2023, IT, healthcare, and manufacturing emerged as the most targeted sectors in terms of ransomware file detections. Both IT and healthcare held the first and second spots of the most ransomware-targeted industries in the fourth quarter of 2022.
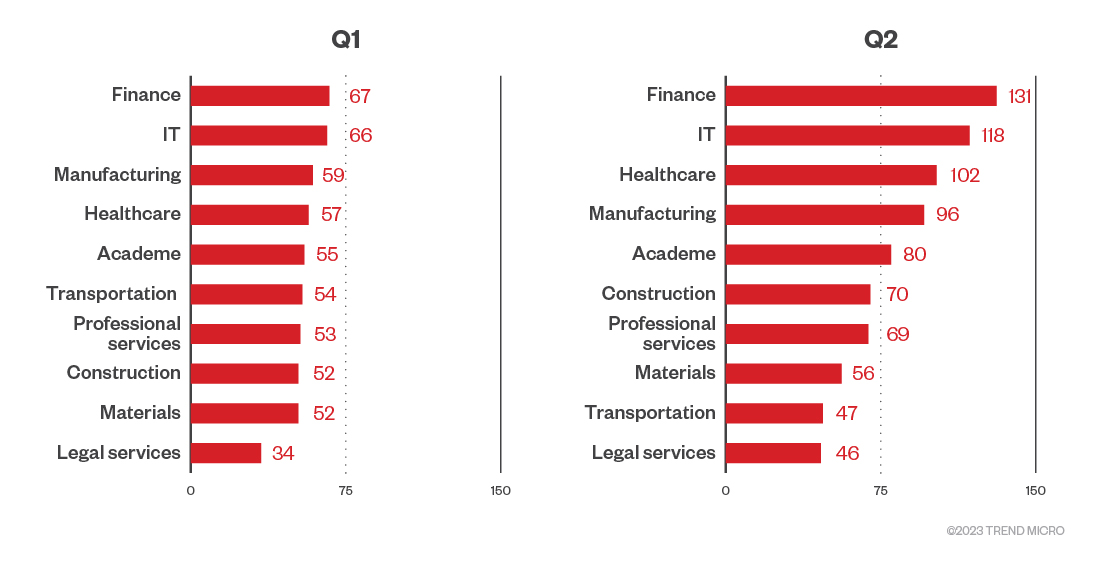
Figure 4. The top 10 industries affected by successful RaaS and extortion attacks in the first and second quarters of 2023
Sources: RaaS and extortion groups’ leak sites and Trend’s OSINT research
LockBit actors mainly focused their attention on IT, finance, and professional services in the first half of the year, based on the ransomware group’s leak site. Three of LockBit’s big-name victims in the first six months of 2023 — Royal Mail, Ion Group, and TSMC — belong in the professional services, IT, and manufacturing sectors, which are part of the top five industries with the most LockBit detections.
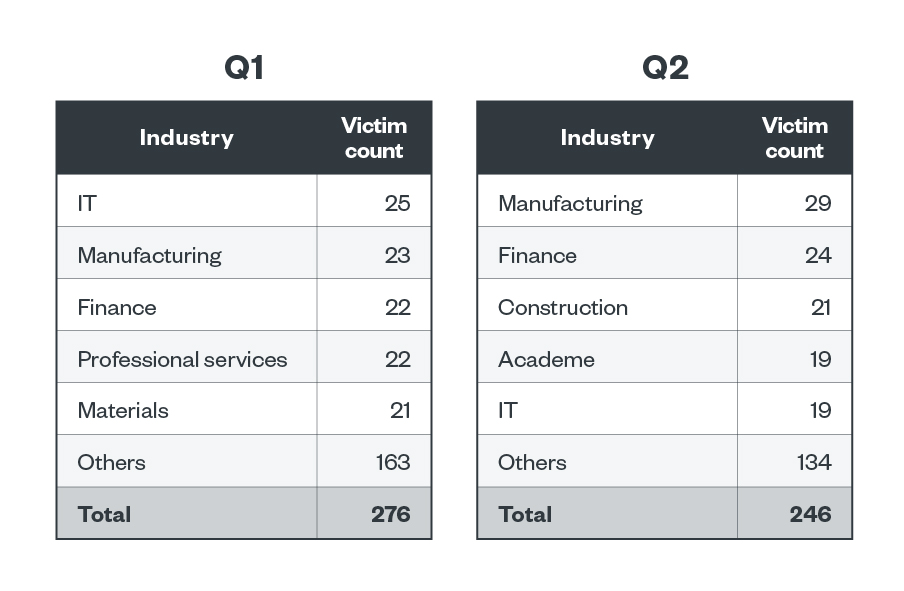
Table 3. The top five industries affected by LockBit’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: LockBit’s leak site and Trend’s OSINT research
Of BlackCat’s 212 total victim count, 11.79% belonged to the finance industry, 8.49% to healthcare, and 8.02% to professional services. Both LockBit and BlackCat had the finance sector in their top three targeted industries’ list in the first half of the year.
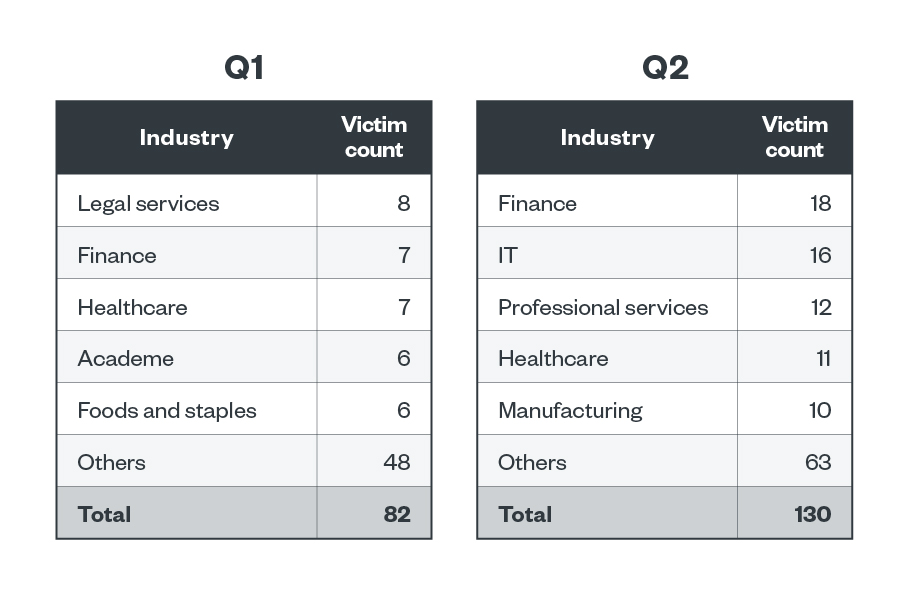
Table 4. The top five industries affected by BlackCat’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: BlackCat’s leak site and Trend's OSINT research
In the first and second quarters of 2023, the Clop ransomware gang’s leak site data revealed that 49 of its victims, which is 24.26% of the total victim count, belonged to the finance sector. Meanwhile, the IT and healthcare industries took 14.36% and 10.89% of victims, respectively.
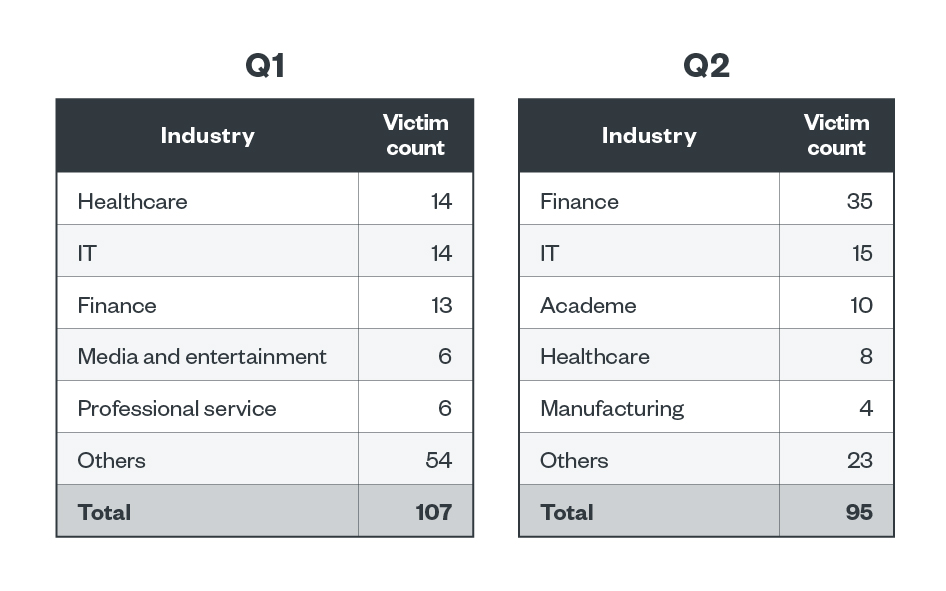
Table 5. The top five industries affected by Clop’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: Clop’s leak site and Trend’s OSINT research
Almost half of all ransomware attacks targeted organizations in the US in the first half of 2023
A deeper look into RaaS and extortion leak site data revealed that US-based organizations took almost half of the total number of ransomware victims with 950 victims in the first half of 2023. This number is 69.9% higher than the second half of 2022, which tallied at 559.
Meanwhile, United Kingdom is a far second with 132 victims, and Canada ranked third with 89 total victims. Most of the countries affected by ransomware attacks are in North America and Europe, with the exception of Australia, India, and Brazil.
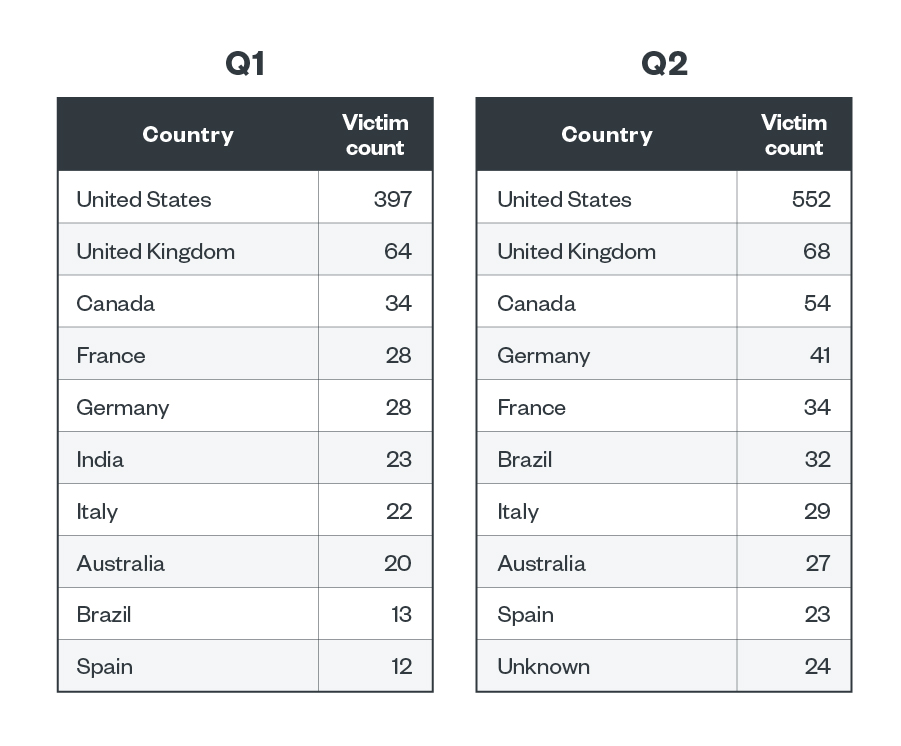
Table 6. The top 10 countries affected by successful RaaS and extortion attacks in the first and second quarters of 2023
Sources: RaaS and extortion groups’ leak sites and Trend's OSINT research
For the first and second quarters of 2023, North America was the most LockBit-targeted region, with 40.9% and 40.7% of the total number of LockBit victims, respectively. Europe and Asia-Pacific occupied the second and third spots in the first half of the year. Europe accounted for 26.8% and 25.2% of LockBit’s total victims in the first and second quarters of the year, while Asia-Pacific had 17% and 16.3%, respectively.
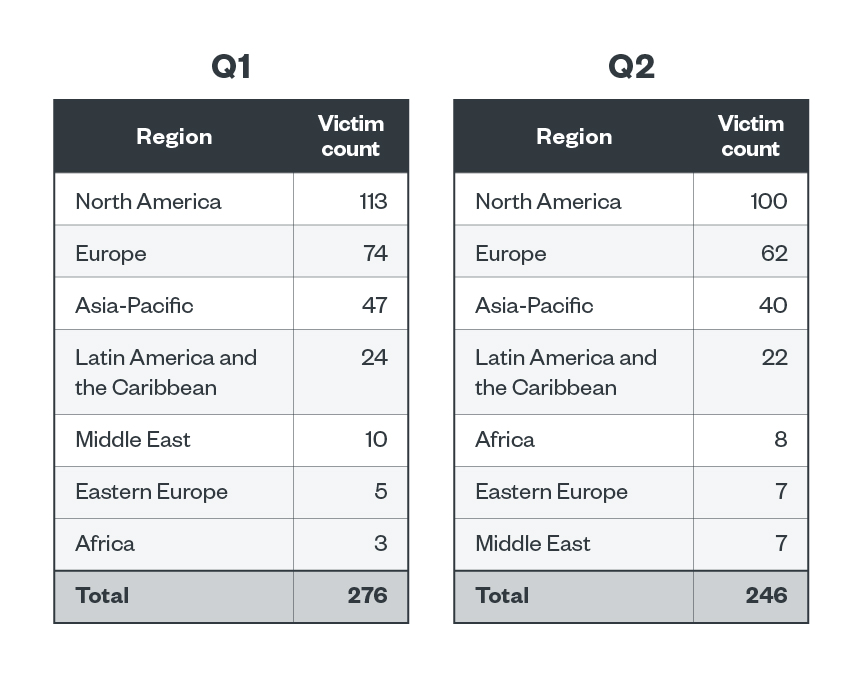
Table 7. The top regions affected by LockBit’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: LockBit’s leak site and Trend’s OSINT research
Meanwhile, for both the first and second quarters of the year, more than half of BlackCat’s victims were from North America, accounting for 56.1% and 57.5% of the total victim count. Alternating in the second and third spots for the first and second quarters of 2023 were Europe and Asia-Pacific. In the first quarter, Europe had a 19.5% share while Asia-Pacific had 13.4%; in the second quarter, APAC overtook Europe with 13.8, and Europe had 12.3%.
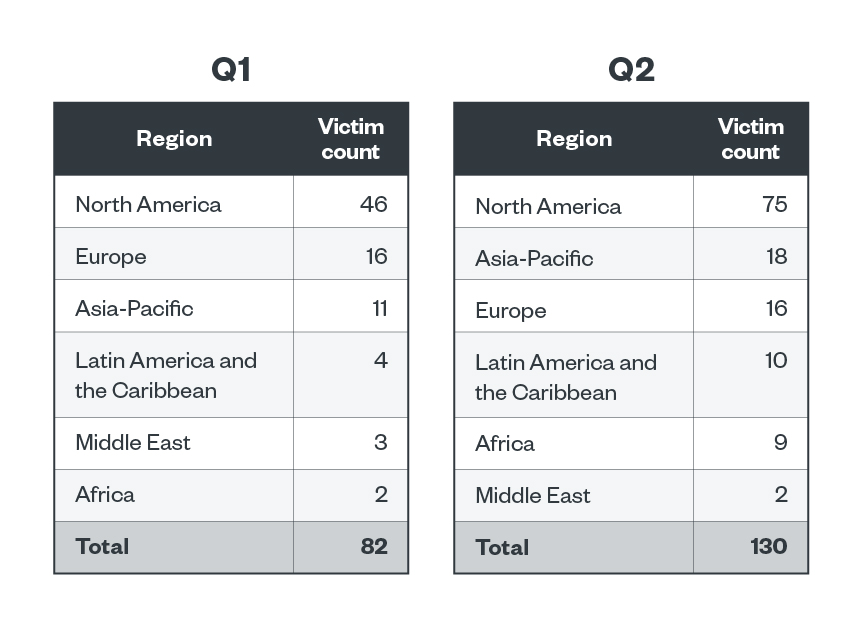
Table 8. The top regions affected by BlackCat’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: BlackCat’s leak site and Trend’s OSINT research
Clop operators also heavily focused on North America in both the first and second quarters of 2023, with 57% and 71.6% of their attacks targeting the region. Europe and Asia-Pacific took the second and third spots for both quarters, albeit with smaller detection counts for both regions. Europe accounted for 15% and 23.2% of Clop attacks for the first and second quarters of the year, while Asia-Pacific accounted for 11.2% and 3.2%
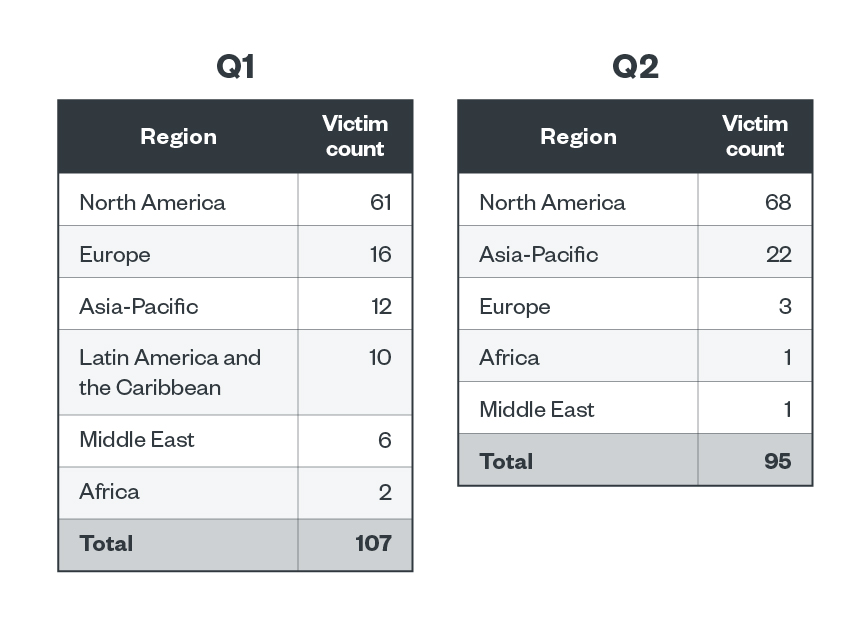
Table 9. The top regions affected by Clop’s successful attacks in terms of victim organizations in the first and second quarters of 2023
Sources: Clop’s leak site and Trend’s OSINT research
Combat ransomware attacks with security recommendations, comprehensive solutions
Ransomware attacks will continue to be the bane of organizations of all sizes. And as ransomware attacks become more evolved and complex, it’s not just ransom demands that will increase through the years: Recovery times are also expected to be longer. In fact, the average recovery time for the retail, restaurant, and hospitality industries was 14.9 days last year — a 91% increase from 2021’s 7.8 days. To effectively counter ransomware attacks, organizations should implement the following security best practices:
- Enable multifactor authentication (MFA). Organizations should implement policies that require employees who access or store company data on their devices to enable MFA as an added layer of protection to prevent unauthorized access to sensitive information.
- Back up your data. Organizations should follow the “3-2-1 rule” to safeguard their important files: Create at least three backup copies in two different file formats, with one of those copies stored off-site.
- Keep systems up to date. Organizations should update all their applications, operating systems, and other software as soon as vendors and developers release patches. Doing so minimizes the opportunities for ransomware actors to exploit vulnerabilities that enable system breaches.
- Verify emails before opening them. Malicious actors rely on tried-and-tested ways to compromise systems, such as using embedded links or executable downloads attached in emails sent to employees to install malware. Organizations should therefore train their employees to be aware of such methods to avoid them.
- Follow established security frameworks. There’s no need to reinvent the proverbial wheel. Organizations can craft cybersecurity strategies based on the security frameworks created by the Center of Internet Security (CIS) and the National Institute of Standards and Technology (NIST). The security measures and best practices outlined in these frameworks can guide members of an organization’s security team in developing their own threat mitigation plans.
Organizations can strengthen their cybersecurity infrastructure through multilayered detection and response solutions that can anticipate and respond to ransomware movements before operators can launch an attack. Trend Vision One™ is equipped with extended detection and response (XDR) capabilities that gather and automatically correlate data across multiple security layers — including email, endpoints, servers, cloud workloads, and networks — to prevent ransomware attack attempts.
Organizations can also benefit from solutions with network detection and response (NDR) capabilities, which can give them broader visibility over their network traffic. Trend Network One™ provides security teams with the critical network telemetry they need to form a more definitive picture of their environment, accelerate their response, and avert future attacks.
The supplementary data sheet for this report, including data from RaaS and extortion groups’ leak sites, Trend's OSINT research, and the Trend Micro Smart Protection Network, can be downloaded here.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Archive
- Phobos Emerges as a Formidable Threat in Q1 2024, LockBit Stays in the Top Spot: Ransomware in Q1 2024
- Rise in Active RaaS Groups Parallel Growing Victim Counts: Ransomware in 2H 2023
- LockBit, BlackCat, and Clop Prevail as Top RAAS Groups: Ransomware in 1H 2023
- LockBit, BlackCat, and Royal Dominate the Ransomware Scene: Ransomware in Q4 2022
- LockBit and Black Basta Are the Most Active RaaS Groups as Victim Count Rises: Ransomware in Q2 and Q3 2022

 Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration
Unveiling AI Agent Vulnerabilities Part III: Data Exfiltration AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity